In today’s hyperconnected world, the battleground has shifted.
From corporate networks to personal devices, cybercriminals are exploiting every vulnerability — and the threats are getting smarter.
Traditional security measures — firewalls, antivirus software, signature-based detection — are no longer enough.
Enter AI-powered cybersecurity: a new frontier where machine learning and automation predict, detect, and neutralize attacks before they strike.
What is AI-Powered Cybersecurity?
At its core, AI-powered cybersecurity leverages:
- Machine Learning (ML): to learn from past data and detect future anomalies.
- Deep Learning (DL): for pattern recognition at scale.
- Natural Language Processing (NLP): to read and understand human communications (e.g., emails, chat logs).
- Generative AI: to simulate and anticipate complex attacks.
Unlike rule-based systems that detect only known threats (via signatures or heuristics), AI continuously adapts to unknown patterns — even when the attack is brand new (zero-day).
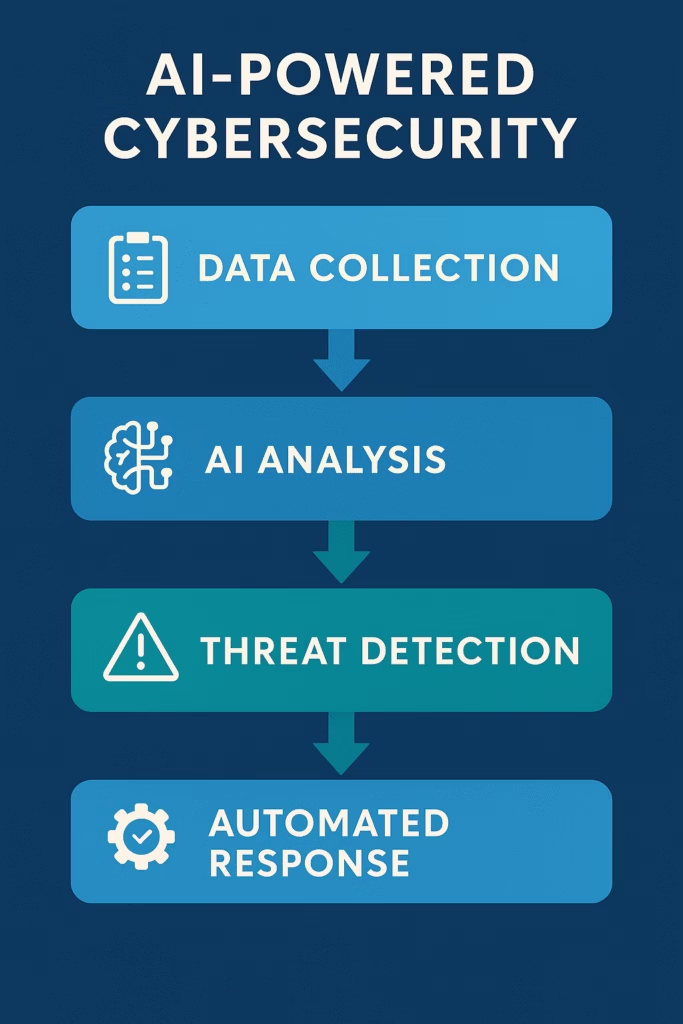
Core Use Cases Where AI is Changing the Game
1. Zero-Day Threat Detection
- Problem: Traditional systems depend on known virus or malware signatures.
- AI Solution:
- AI models learn normal behavior on networks and endpoints.
- When unusual patterns occur (e.g., sudden file encryption, unfamiliar executable behavior), they flag or block them instantly — even if it’s never been seen before.
Example:
A company’s network traffic shows a sudden surge of outbound data packets from a server that never sends data externally.
- Traditional systems miss it (no known signature).
- AI anomaly detection raises a red flag within seconds.
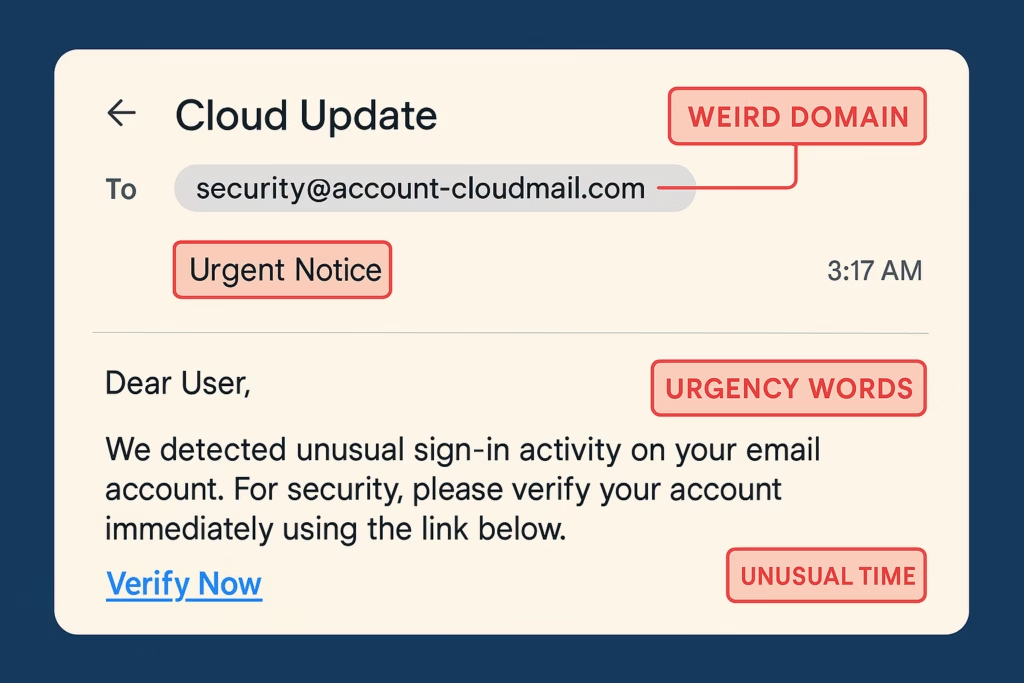
2. Phishing Attempt Detection
- Problem: Phishing emails evolve constantly to bypass traditional spam filters.
- AI Solution:
- NLP models analyze email metadata, text patterns, link destinations, and sender behavior.
- They spot inconsistencies (e.g., domain spoofing, linguistic anomalies) that humans may miss.
Example:
An email says, “Urgent password reset” from “micros0ft-support.com”.
- AI notices domain spoofing.
- Detects an unusual tone in the email (“fear urgency” signal).
- Blocks or quarantines the email before reaching the user.
3. Securing Edge Networks
- Problem: IoT devices and remote workers create huge decentralized attack surfaces.
- AI Solution:
- Deploy lightweight AI agents on edge devices.
- Monitor real-time behavior without relying solely on central servers.
- Detect breaches even if the device is offline from the core network.
Example:
A smart thermostat behaves unusually, sending frequent outbound packets to unknown servers.
- AI agent on the device detects deviation from baseline behavior.
- Initiates device isolation automatically to contain potential breaches.
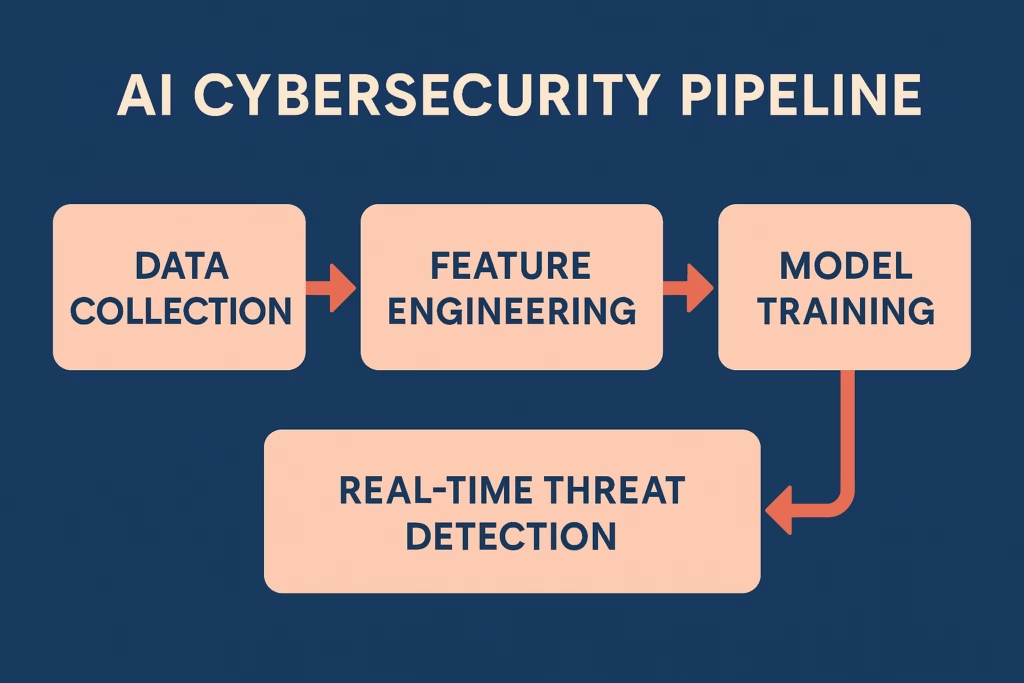
Technical Deep Dive: How AI Detects Cyber Threats
| Layer | Technology | Role |
|---|---|---|
| Data Collection | Sensors, logs, telemetry from endpoints and networks | Raw input for AI training |
| Feature Extraction | Statistical analysis, NLP processing, image recognition | Distill important threat indicators |
| Model Training | Supervised/Unsupervised Learning | Learn normal vs abnormal behavior |
| Anomaly Detection | Clustering, outlier analysis | Spot potential threats |
| Automated Response | Policy engines, SOAR platforms | Trigger auto-containment, alerts, or countermeasures |
Example ML Models in Use:
- Random Forests: Predict malicious behavior based on network activity features.
- Autoencoders: Find anomalies in system logs by reconstructing expected behaviors.
- Graph Neural Networks: Map interactions and find suspicious connections between users, devices, and apps.
Real-World Applications and Success Stories
- Darktrace uses self-learning AI to spot insider threats and stealthy ransomware before encryption kicks off.
- Vectra AI applies AI-driven network detection to identify compromised accounts based on behavior drift.
- Microsoft 365 Defender integrates AI models to detect phishing attacks across Outlook, SharePoint, and OneDrive.
Result?
Companies see a 60-80% faster breach detection rate and a dramatic drop in manual security operations overhead.
Challenges and Risks
| Challenge | Why It Matters | How to Mitigate |
|---|---|---|
| False Positives | AI sometimes flags harmless activity as threats. | Improve data quality; retrain models often. |
| Model Drift | AI models lose accuracy as attacker tactics evolve. | Continuous retraining and feedback loops. |
| Adversarial Attacks | Hackers can try to fool AI models. | Use adversarial training, model robustness techniques. |
Future of AI-Powered Cybersecurity
Looking ahead, AI will:
- Predict attacks before they happen by analyzing minor deviations.
- Collaborate with human analysts in hybrid SOCs (Security Operations Centers).
- Integrate with decentralized security frameworks using blockchain and self-sovereign identity (SSI).
Imagine AI agents negotiating access controls based on real-time risk — fully autonomously.
Conclusion: The AI Advantage in Cybersecurity
Cyberattacks are becoming faster, stealthier, and more complex.
But AI is leveling the playing field by detecting the invisible, predicting the unpredictable, and responding at machine speed.
For businesses, governments, and even individuals, adopting AI-powered cybersecurity isn’t just an option —
it’s a survival strategy for the digital age.
If you’re not using AI to defend your assets, chances are, someone’s using AI to attack them.





